Background
Spectre CVE-2017-5715 Meltdown CVE-2017-5754. Install Windows Server Patch
Finally on 4th of January 2018 Microsoft released patch for processors vulnerabilities. If you’re not sure what is background of that security issue check my last two posts:
- Vulnerabilities summary for Spectre CVE-2017-5715 Meltdown CVE-2017-5754 – LINK
- How to check with Powershell if your system is affected – LINK
In this article I will check once again vulnerability Spectre CVE-2017-5715 Meltdown CVE-2017-5754. Install Windows Server Patch will be performed to check effect and do performance test after that. Let’s see what will happen on Microsoft Windows 2016 with related path.
Information
After check system vulnerability with Powershell module, in PS window additional information was shown. There was also the LINK Microsoft posted there solution to prevent security problem with processors. There is also table with available KB which should be installed:
| Operating system version | Update KB |
| Windows Server, version 1709 (Server Core Installation) | 4056892 |
| Windows Server 2016 | 4056890 |
| Windows Server 2012 R2 | 4056898 |
| Windows Server 2012 | Not available |
| Windows Server 2008 R2 | 4056897 |
| Windows Server 2008 | Not available |
In my case 4056890 KB is needed for Windows Server 2016. KB will be downloaded automatically on second Tuesday of Month. If we need to download it on demand just go to Update Catalog search for KB4056890 and choose correct patch version. Amount data to download is 1,2 GB.
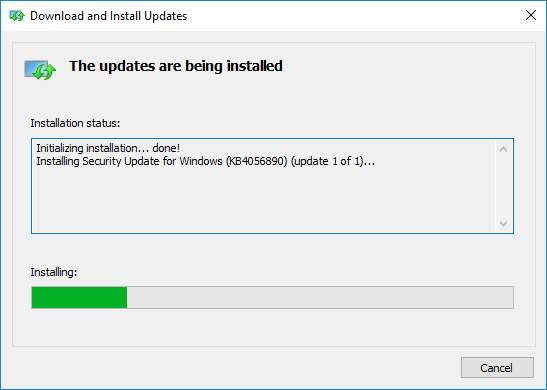
Before and after patch installation I will do 3 things:
- Check vulnerability with Powershell,
- Test performance using PassMark Software,
- Test performance with SunSpider.
It should be great stuff to compare results.
Comparison before and after patch installation
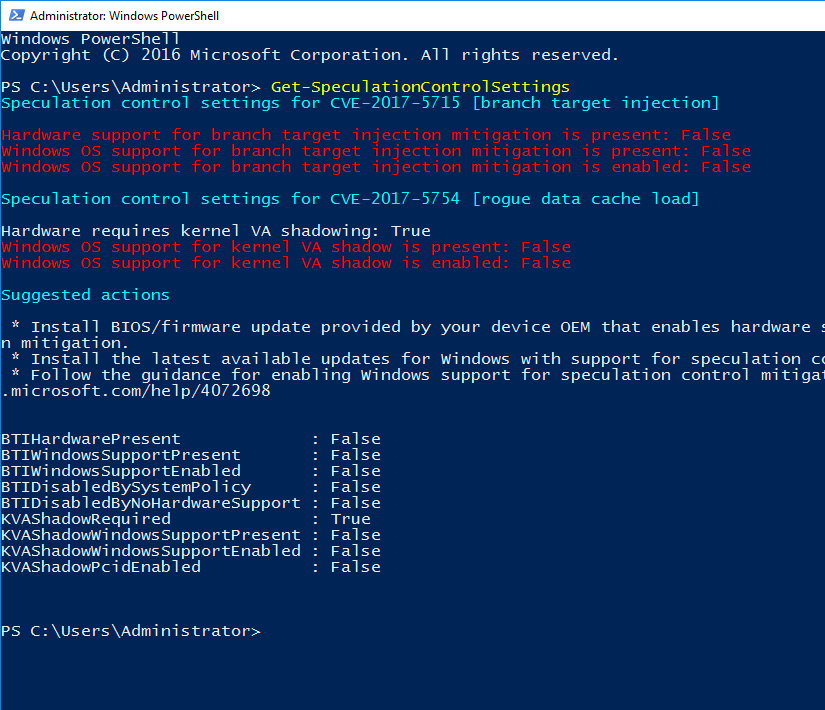
Powershell vulnerability check BEFORE:
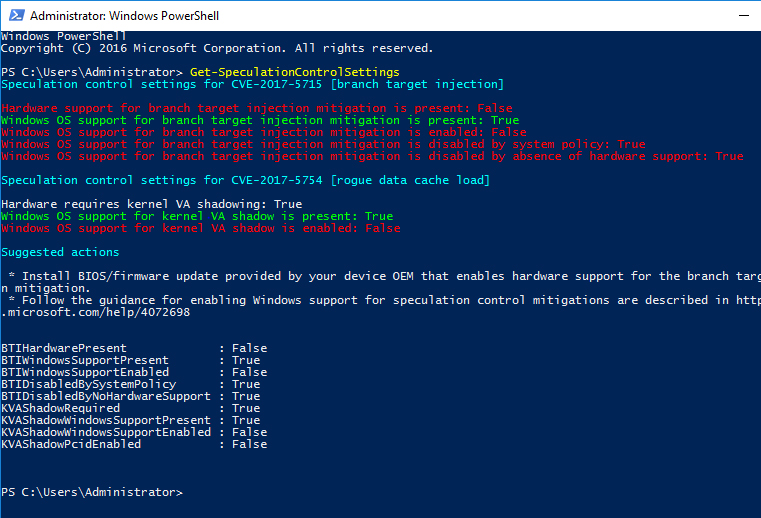
Powershell vulnerability check AFTER:
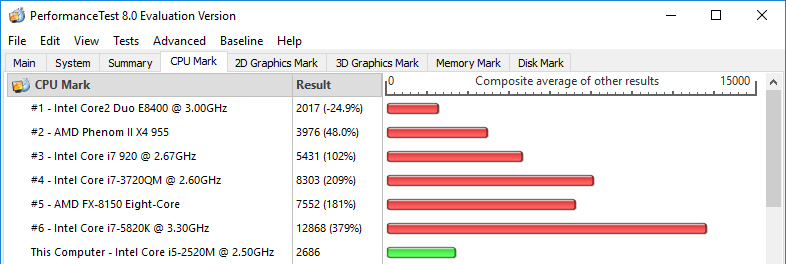
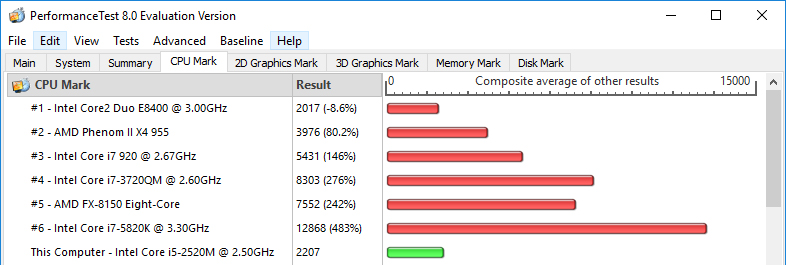
PassMark performance check BEFORE:
PassMark performance check AFTER:
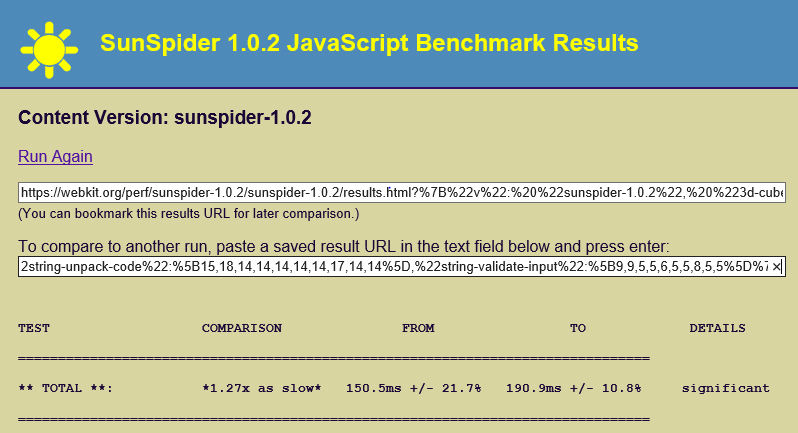
SunSpider performance check before and after:
Conclusion
- Patch installation changed security values and Powershell check result is better after patch implementation,
- PassMark shown 2686 points before and 2207 after patch implementation. It’s around 18% less,
- SunSpider shown 150,5 ms before and 190,9 after patch implementation. It’s around 27% slower.
Unfortunately, values are not the best but also not that worse that I can expect. Internet said even about 60% difference in some cases. I have 18% and 27% change to worse. Is that a lot? For my virtual environment where I’m performing only tests – not really because I don’t even need that patch. But for real infrastructures? Think about yours environments and ask yourself…




