Windows domain administrator account theft is possible
In my previous Question and Answer post I talked about hack Windows local administrator account , which is possible with playing on Utilman and Ease of Access. Following this article you can simply change password of any of local accounts or create a new one. It’s really old an known vulnerability, but it’s still work even on newest Windows Server 2016. Key information is that if you don’t care about physical access to your server (physical but also management console and virtual console if it’s a vm) someone can access OS as local administrator. Not good. Worse thing is that local server administrator can also steal domain admin account, or any other. Dangerous is most higher if admins in your environments use to leave RDP session on server instead of sign out. If this situation appears, this post is 100% actual. Windows domain administrator account theft is possible
What is the background?
Let’s imagine that someone who used Utilman vulnerability are already logged into one of your server and you don’t know that. Other of administrator just end his work, disconnect RDP session (not sign out!) and go home. He has domain administrator role so in other words on the server domain administrator account is still logged in. It’s time for our villain. Why?
Procedure to steal Windows domain administrator account
Our black character who already has access to server as local administrator can download simple tool called Process Hacker and install it or run from portable version. In program window all active processes are visible as in Task Manager build in Windows OS but Process Hacker can something more.
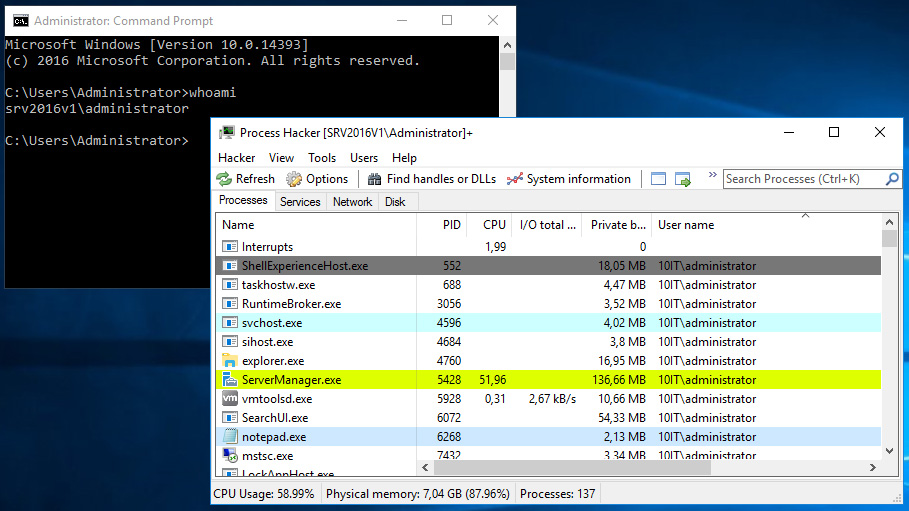
If you go to process started as other domain account (remember that you’re login in as local administrator) you can right click on it and choose Miscellaneous and Run as this user… option.
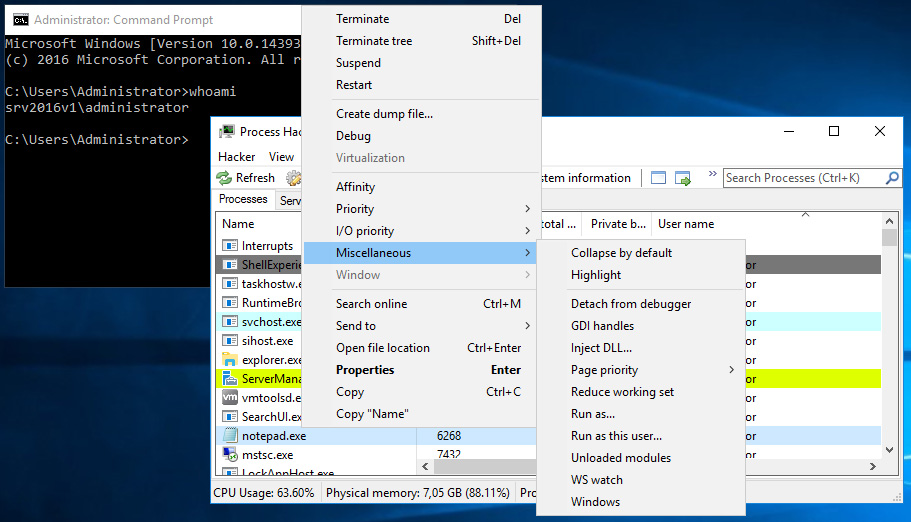
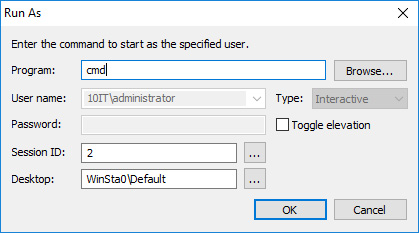
In newly opened window just type cmd and confirm by clicking OK.
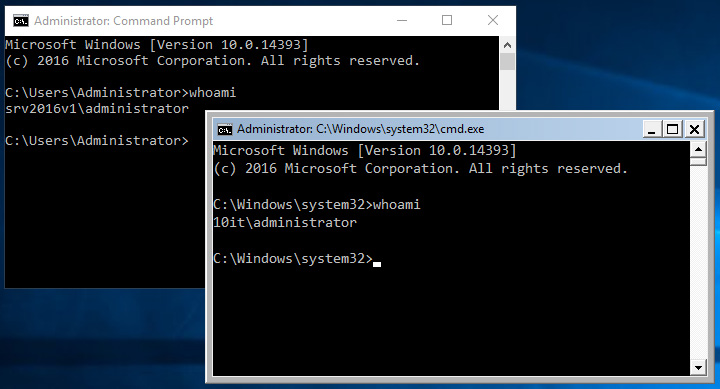
Now go to new cmd window and type whoami to determine as who it started.
Is that really dangerous?
Yes it is. If you have cmd started as domain administrator you can do everything. Create new domain account which is member of domain admins group and then log as this user? No problem. Start powershell as domain admin from cmd and remotely manage all computer in domain? Also not so hard to do.
Conclusion
Always take care about physical access to servers. In any case if it’s a physical access, administration with management console or console in hypervisor, always have knowledge who can manage them to avoid surprises.
Take care!




